binTree Information leakage prevention software
nowadays,what is the most important resources for enterprises? First, the core technology, the seconde is to build up the network of customers. Core technology may be had spend a lot of money to buy ,or spend plentiful time to research and development. The establishment of a customer’s network business need a lot of money , time and energy,too. However, little u disk, mobile hard disk, floppy disk, or Burn Disc, can be easily taken them away. Business is war, perhaps, disgruntled employees of companies are preparing to leave the company, he will take away business-critical information. These data will eventually fall into a competitor you can not control, perhaps, your staff has been serving for your competitors , perhaps, he join your company is to get your company to the company’s core information.
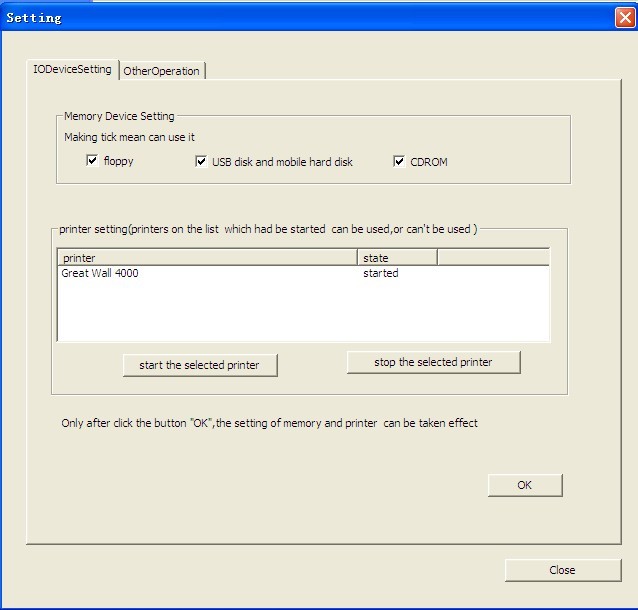
this software is to prevent disclosure of corporate information . It is your an invisible lock of your computer. Without your permission, your employees can not be used u disk, mobile hard disk, floppy disk, Burn Disc , Printer. At the same time it maintains the flexibility to use these devices when needed. managers enter a password, start these device , you can use these. After using them , you can disable these them. At the same time, you can use this software to set which network printer can bu use , the network printer be in front of you or in front of the manager, your employees must be to get things printed. You can prevent the printer be abused and prevent the important data to be printed to take away. Even if there are other printers on the network,without your agreement,he/she can’t use it .
This security software using the underlying technology to write, direct control of the hardware, it consumes few resources,. It uses some very advanced technology, and it itself can not be closed, will be forced to auto-start, there is a strong security